Most business owners know what a phishing attack is. And this awareness has lowered the success rate of many phishing attacks. But hackers, being hackers have adapted and evolved with a new and growing type of account takeover attack. It is called lateral phishing, and here’s what you need to know.
What is Lateral Phishing?
Regular phishing attacks generally send an email from an account designed to look like a legitimate business. With more people aware of this scheme, it is getting harder to fool people.
Hackers have found a workaround to this problem by first taking control of an account in an organization. Once they are successful, they leverage this account to launch the attacks.
The success rate of this type of attack is almost guaranteed because the recipient recognizes the email account. Everyone from contacts within the company to partners, vendors, and personal friends outside of the organization can be victimized.
Researchers from Barracuda, UC Berkeley and UC San Diego studied lateral phishing over the past year. The study and report looked at how this form of attack is becoming so pervasive. This large-scale study of lateral phishing attacks has a data set covering 113 million employee-sent emails from 92 enterprise organizations.
Of the 154 hijacked accounts the researchers identified, hackers were able to send hundreds of lateral phishing emails to more than 100,000 unique recipients.
Here is a word from Barracuda about lateral fishing and 13 email threat types to know about right now:
Key Takeaways on Lateral Phishing
Lateral phishing attacks are increasingly becoming a significant cybersecurity concern for businesses. These covert attacks, which exploit compromised internal accounts to target unsuspecting employees and partner organizations, can have severe ramifications. Here are the key takeaways to understand the gravity and nuances of this threat:
- Prevalence and Reach:
- 1 in 7 organizations encountered lateral phishing in the past seven months.
- Among these affected organizations, over 60% had multiple accounts compromised.
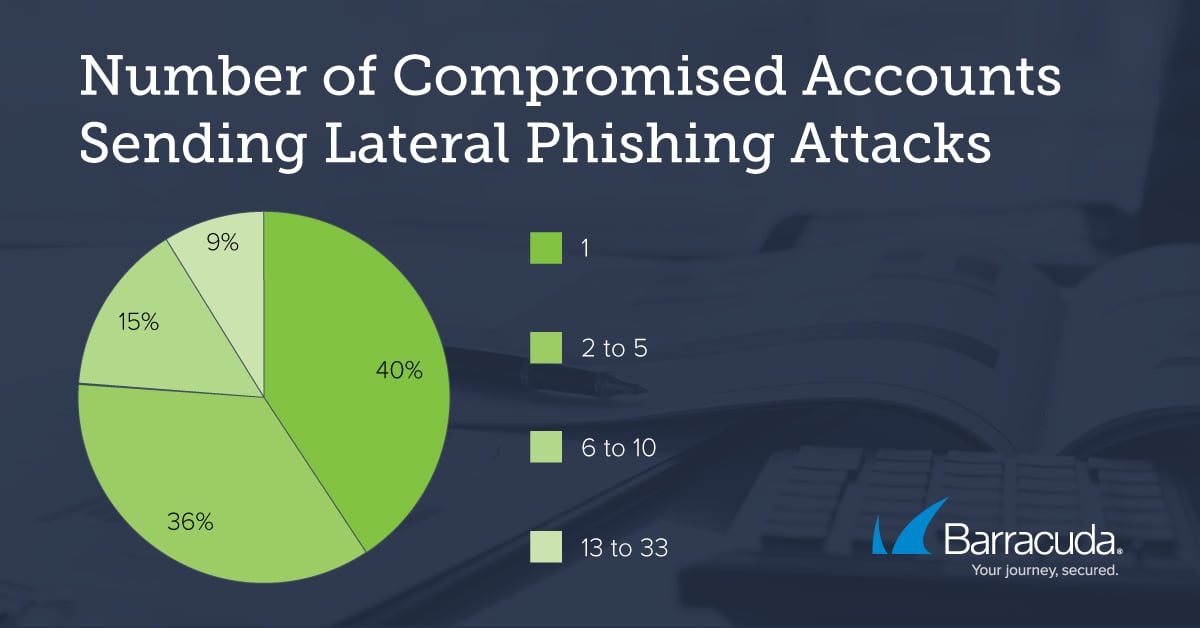
- Attack Distribution:
- When hackers initiate these attacks, they don’t hold back. A whopping 40% of the 100K recipients in the study were within the same company.
- The external fallout is even greater, with 60K or 60% of these emails reaching partner organizations, potentially jeopardizing inter-company trust.
- Reputational and Financial Impact:
- The direct financial costs of such attacks are evident. However, there’s a lurking danger in the potential reputational damage that can lead to further financial strain. As trust erodes, partner organizations might question the security protocols in place.
- Underreporting is a Concern:
- An alarming 42% of these phishing incidents go unreported. This gap in reporting can lead to unchecked propagation of the phishing attack, not just within the company but potentially across its network of partner organizations.
- Tactics Employed by Hackers:
- They majorly employ two narratives to dupe victims:
- Generic Messages (63%): These are broad-based lures and often include prompts like “account error” or a “shared document.”
- Tailored Content (37%): A more insidious approach where the content is specifically tailored, often targeting enterprise-related topics or aspects unique to a specific organization.
- They majorly employ two narratives to dupe victims:
Understanding these key takeaways offers a clearer perspective on the lateral phishing landscape and the urgency needed to address it.
Traditional Phishing vs. Lateral Phishing: A Comparative Analysis

This table provides a clear understanding of phishing and lateral phishing. It also highlights the unique dangers of both and how you can prevent them happening. It’s an excellent resource for businesses wanting to educate their employees on the differences and ensure they take the necessary precautions against both.
| Feature/Aspect | Traditional Phishing | Lateral Phishing |
|---|---|---|
| Basic Mechanism | Send emails from accounts resembling legitimate businesses. | First, take control of an organization's internal account and then launch attacks. |
| Trustworthiness | Lower success due to increasing awareness. | Higher success rate since the email comes from a recognized internal account. |
| Primary Targets | General public. | Internal employees, partners, vendors, and friends linked to the compromised account. |
| Email Content Type | Often generic. | Can be both generic and specifically tailored to the organization. |
| Detection | Check sender properties or email headers. | Requires checking the actual destination of a link in the email. |
| Defensive Measures | Basic email-checking protocols might suffice. | Requires advanced detection techniques, increased awareness, and two-factor authentication. |
Protecting You and Your Small Business Against Lateral Phishing
As the threat of lateral phishing grows, the importance of implementing protective measures becomes paramount. Businesses must not only understand the nature of this threat but also be equipped with the right tools and knowledge to counteract it.
According to Asaf Cidon, Vice President of Content Security Services at Barracuda Networks, more awareness is the key to defending against lateral phishing.
Although this advice seems obvious, double-checking your emails before opening them can prevent an attack. But lateral phishing has introduced another twist to the problem. Even if you double-check, you think you are opening an email from a colleague. So, increased awareness is in order.
Cidon has three recommendations: security awareness training, advanced detection techniques, and two-factor authentication.
Security Awareness Training

Security awareness training shouldn’t be a one-off event because hackers are always evolving. Cidon says telling your staff to check the sender properties or email headers like regular phishing attacks will not work.
With lateral phishing, they have to check the actual destination of a link in any email.
Advanced Detection Techniques

Lateral phishing is making it much more difficult to detect an attack, even for trained users.
Your business needs to invest in advanced detection techniques and services. These solutions use artificial intelligence and machine learning to identify phishing emails automatically.
Two-factor Authentication

Cidon says using a strong two-factor authentication (2FA), such as a two-factor authentication app or a hardware-based token is key. He goes on to say even non-hardware based 2FA can provide some protection.
As with any security measure, the goal is to put enough barriers between you and the attackers. If these barriers do the job, they will deter the majority of hackers. But as headline after headline show, the value of the information you hold will dictate the effort hackers put in.
Implementing Robust Email Security Measures
To fortify defenses against lateral phishing attacks, businesses must implement robust email security measures that go beyond basic filters and antivirus software.
Integrating advanced security solutions that utilize artificial intelligence (AI) and machine learning can significantly enhance an organization’s ability to detect and prevent sophisticated phishing attempts. Secure email gateways and DMARC policies are crucial for authenticating email senders and verifying that the emails originate from legitimate sources.
Additionally, employing email security solutions that offer behavioral analysis can help identify unusual patterns in email activity, flagging potential lateral phishing attacks before they reach the recipient. Training employees to recognize the signs of phishing and to report them promptly is equally important.
Creating a Culture of Security Awareness
The human element is often the weakest link in cybersecurity. Creating a culture of security awareness within an organization can empower employees to act as the first line of defense against lateral phishing attacks.
This involves conducting regular, interactive training sessions that simulate phishing scenarios, helping staff to recognize and respond to threats effectively. Encourage employees to adopt a healthy skepticism towards emails, even those that appear to come from colleagues, and to verify the authenticity of requests through direct communication.
Promoting an environment where employees feel comfortable reporting suspicious emails can significantly reduce the risk and impact of successful phishing attacks.
Regular Monitoring and Incident Response Planning
Continuous monitoring of network and email activity is essential for early detection of lateral phishing and other cyber threats. Implementing a system that alerts IT personnel to suspicious behavior can help catch attacks in progress, minimizing damage.
An effective incident response plan is crucial for quickly containing and mitigating the impact of a security breach.
This plan should outline specific steps to isolate compromised accounts, notify affected parties, and conduct a thorough investigation to prevent future incidents. Regular security audits and vulnerability assessments are also vital for identifying and remedying potential entry points for attackers.
Encouraging Reporting and Open Communication

To combat lateral phishing effectively, organizations must foster a culture where reporting suspicious emails is encouraged and straightforward. Providing clear instructions on how to report phishing attempts, whether through a dedicated email address, reporting button, or IT hotline, can facilitate this process.
Open communication about the importance of reporting and the role it plays in protecting the organization can help to ensure that employees do not hesitate to flag potential threats. Recognizing and rewarding vigilant behavior can further reinforce the value of proactive reporting.
Partnering with Cybersecurity Experts
Given the sophistication of lateral phishing attacks, many businesses, particularly small and medium-sized enterprises, may benefit from partnering with external cybersecurity experts. These specialists can offer advanced email security services, tailored advice, and continuous monitoring to guard against phishing and other cyber threats.
Leveraging the expertise of managed security service providers can provide businesses with access to the latest security technologies and threat intelligence, enhancing their overall cybersecurity posture.
Such partnerships can also free up internal resources, allowing companies to focus on their core activities while ensuring their defenses against lateral phishing are as strong as possible.
By addressing these critical aspects, businesses can significantly improve their resilience against lateral phishing attacks, safeguarding their data, reputation, and relationships with clients and partners.
Implementing comprehensive email security measures, fostering a security-aware culture, maintaining vigilance through regular monitoring, and seeking expert guidance are all essential strategies in the fight against this evolving cyber threat.
Whether you are aware of lateral phishing attacks or not, this is a worthwhile read. You can find the report here.
Image: Depositphotos.com
This article, "Lateral Phishing: The Silent Threat to Your Small Business" was first published on Small Business Trends
------------Read More
By: Michael Guta
Title: Lateral Phishing: The Silent Threat to Your Small Business
Sourced From: smallbiztrends.com/2024/02/lateral-phishing.html
Published Date: Tue, 06 Feb 2024 14:04:14 +0000
.png)