The recent security breach that affected LastPass has caused ripples across the industry. Norton Password Manager suffered a password stuffing attack, while Bitwarden users have been targeted by phishing ads.
Many users are worried whether hackers break into their password vaults. They are encrypted with zero-knowledge, they should be safe, right? The answer is not that simple, as there are other factors that affect the outcome, one of which is the cryptography system that is employed by the service. A key component of this is KDF.
What is KDF?
KDF stands for Key Derivation Function, it is a cryptographic algorithm that derives secret keys from values such as passwords, master keys, etc,. This is how password managers create an encryption key, from your master password, to protect your password vault.
The function also has other uses. You may be familiar with the terms hashing, salt, pepper, etc. Most websites don't just store (hashed into a value) passwords at their face value, usually they add a random string to passwords to protect them from dictionary attacks, this process is called salting. This data is then hashed and stored, so even if a hacker manages to gain access to the passwords, they won't be able to use the data since the salting process changed the hashes of the original password, so it can't be cracked as easily.
KDF does a similar thing, this depends on the number of iterations it is set to, aka as rounds. e.g. 100,000 rounds to rehash the values. It stretches your key, thus slowing down the process of guessing the password, making it more expensive and difficult to compute. In a nutshell, the higher the number of iterations, the harder it is for hackers to brute-force your decryption key to get into your password vault. The commonly used KDF algorithm is PBKDF2, though there are others like Argon2, Scrypt, Bcrypt.
A Senior Security Engineer at Yahoo, Jeremi Gosney argued that a strong, unique master password will protect users more than a high count of KDF iterations can, but also said that the latter will also help secure users who don't use a very strong password.
Let's look back at the LastPass data breach. The password manager service had set the default iterations count to 100,000 for new accounts, but many old accounts were stuck at 5,000. Security experts had criticized the company for sticking with this, and said that even 100,000 iterations wasn't good enough. This was not the only reason for the LastPass data breach, they had more issues related to the security of their systems, how they got breached initially, not encrypting user data such as URLs, etc. But, what we have learned from recent incidents, is that we have to be extra careful to protect our data.
Bitwarden to increase its server-side iterations to 600,000
It is important to note that there are 2 kinds of iterations done by Bitwarden; one on the client side (that is, your computer), and the other is done on the server side. A white paper published by the password manager service indicates that it does 200,001 rounds, i.e. 100,000 + 1 using PBKDF2 SHA-256 on the client side, and 100,000 on the server's side.
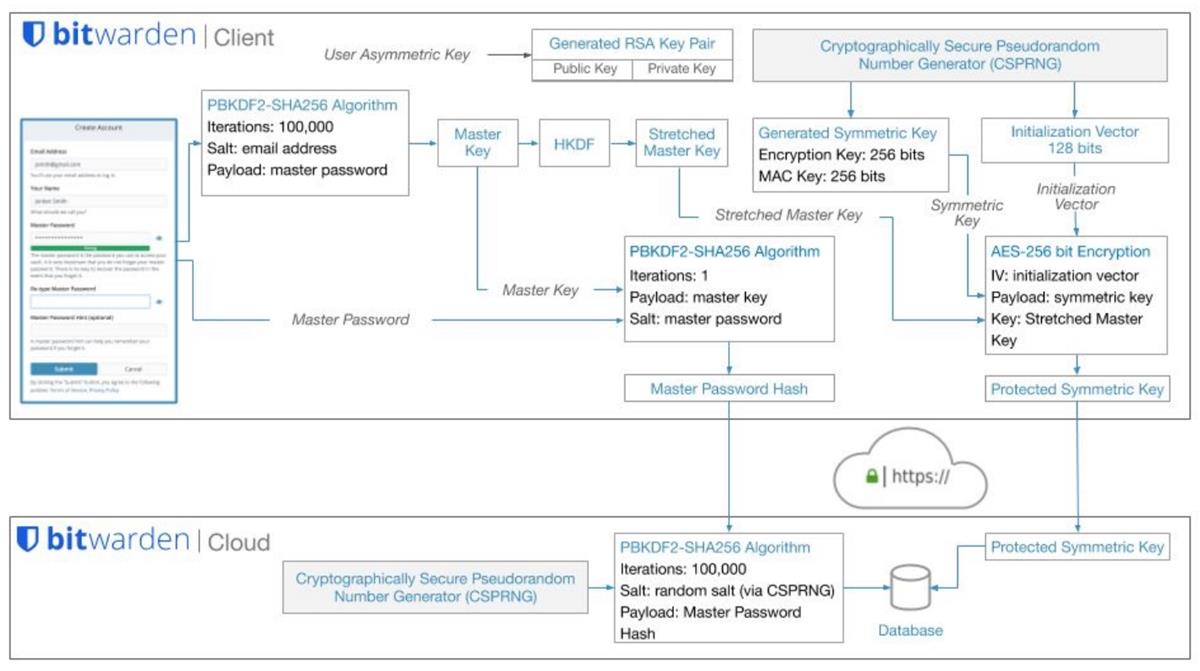
Wladimir Palant, the creator of AdBlock Plus, has pointed out that Bitwarden was not actually running 100,000 on the server side for the encryption key, it is only done for the master password. The client-side on the other hand handles both. Now, here is the thing. Bitwarden's default KDF iterations is actually pretty low, it sits at 5,000 server-side iterations. Palant said this flaw meant that the security level of Bitwarden is identical to what LastPass had.
Security expert, Dmitry Chestnykh, had mentioned this problem in 2020, yet it still remains unresolved. Many users have asked the company to address this issue. As a matter of fact, users have been requesting better algorithms, such as Argon2, since March 2018.
Bitwarden replied to a user on Mastodon, saying that they would increase the count to protect user data. It is not clear whether this will affect existing user accounts, the company has responded to queries that it is working on it. But you don't have to wait for them to act, you can change it manually right now.
Warning: You are advised to export your vault (backup) before trying the following. Users who have the Bitwarden browser extension users or the mobile app can go the Settings > Export Vault. The desktop client lets you do the same from the File menu > Export Vault. Once you change the KDF iteration count you will be logged out of all clients. That's because the encryption key is changed. Using a high KDF count will cause your password vault to open more slowly. Please refer to the official support page for more information.
How to change the KDF iterations count in Bitwarden Password Manager
1. Login to your Bitwarden vault.
2. Click on your profile in the top right corner.
3. Select Account Settings.
4. Switch to the Security tab. The URL is https://vault.bitwarden.com/#/settings/security/security-keys.
5. The option that we are looking for is the KDF Iterations. It is set to 5000 by default, even though a note below the box states that the recommended value is 100,000 or more.
6. Click on the box and type 600,000. Enter your master password in the corresponding field.
7. Hit the Change KDF button.
Note: You will be logged out of your account, and a message will pop up to indicate that your encryption key has changed.
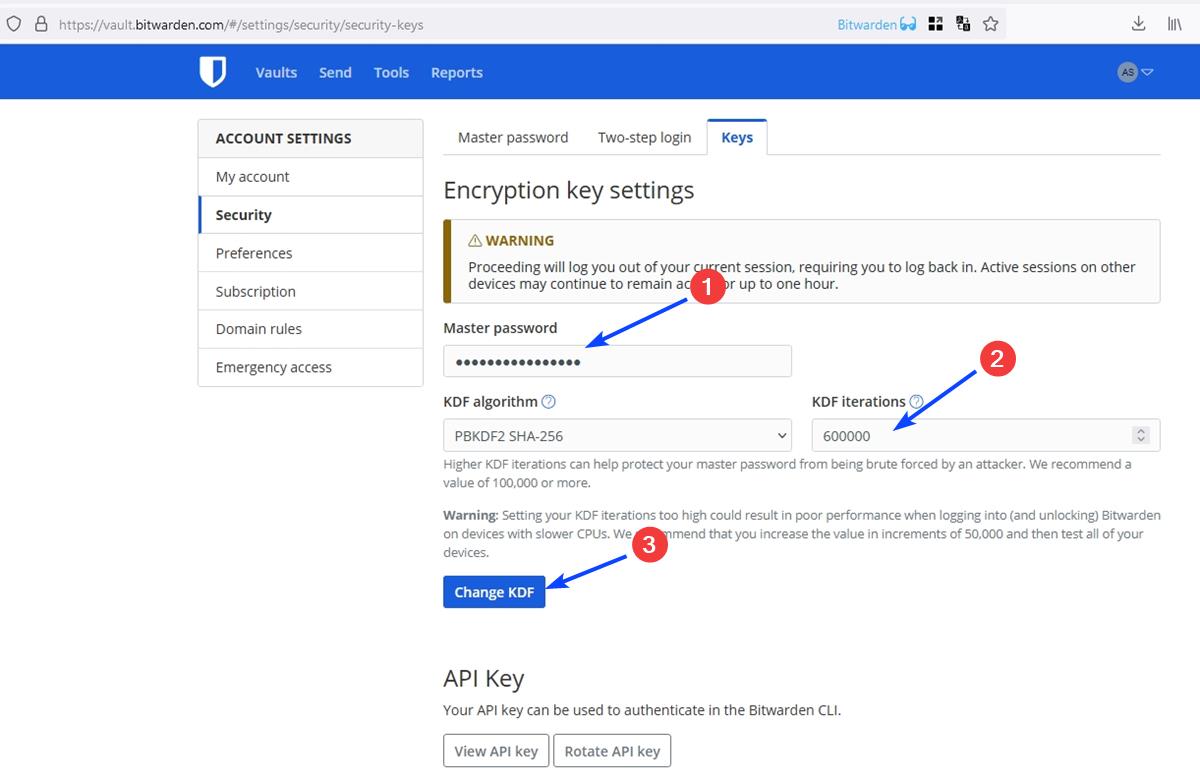
Why 600,000? It is the number of KDF iterations that the Open Web Application Security Project (OWASP) recommends. Until recently, OWASP actually recommended 310,000 as the default number of iterations. But that seems to have nearly doubled over the past week. Even Bitwarden's message on Mastodon does mention that the initial plan was to set the KDF iterations to 350,000, but then they decided to go with 600,000.
While you are at it, I'd also recommend changing the clipboard behavior of Bitwarden's browser extension. Click the add-on's button > Settings > Options > Clear Clipboard. By default, this is set to never clear the clipboard, change it to 1 Minute or whatever suits you. (h/t Techspot)
I also recommend reading Palant's recent article about how password strength works.
Thank you for being a Ghacks reader. The post Bitwarden's Latest Update Takes Security to the Next Level appeared first on gHacks Technology News.
------------Read More
By: Ashwin
Title: Bitwarden's Latest Update Takes Security to the Next Level
Sourced From: www.ghacks.net/2023/02/02/bitwarden-to-increase-its-server-side-iterations-to-600000-heres-how-to-set-it-manually/
Published Date: Thu, 02 Feb 2023 09:00:58 +0000
Did you miss our previous article...
https://trendinginbusiness.business/technology/how-is-prek-utilizing-childrens-edtech
.png)





